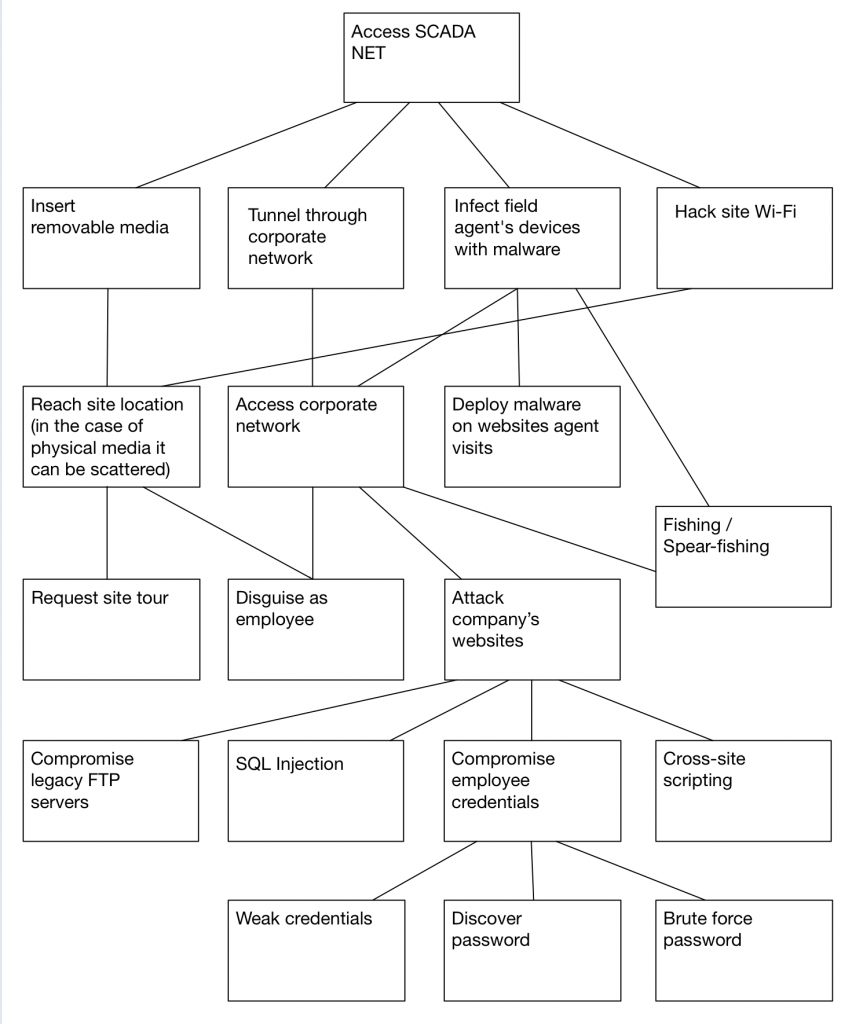
Projects
Current Projects
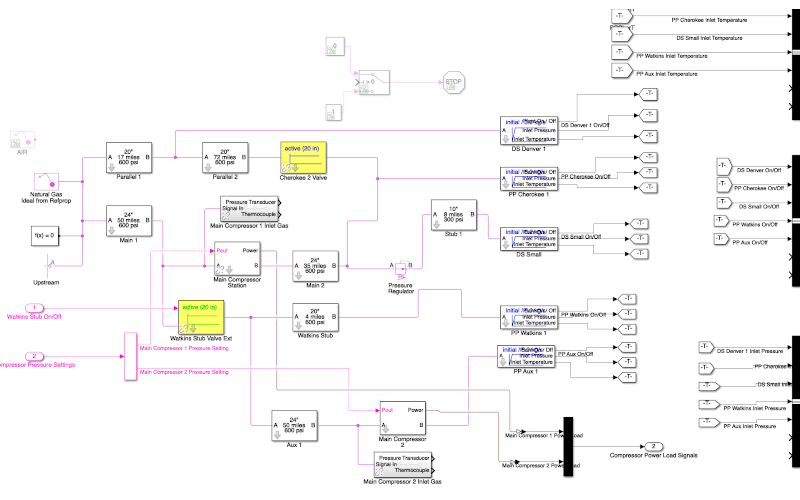
Simulated & Virtual SCADA Systems
The simulation of SCADA systems for security study can be a complex but rewarding practice. This project focuses on developing accurate ways to simulate the physical nature of energy system dynamics as well as vitualizing the control used to manage these systems. Virtualization of these SCADA systems also allows us to study their security in a low cost and safe manner.
Anomaly Detection of SCADA Packet Captures
Packet captures of SCADA traffic typically are comprised of MODBUS traffic. MODBUS is a standard protocol for these systems that have been in place for over 30 years. These packet captures can be used as a way to characterize a SCADA system and observe abnormal changes that could signal or forewarn a cyber attack.