
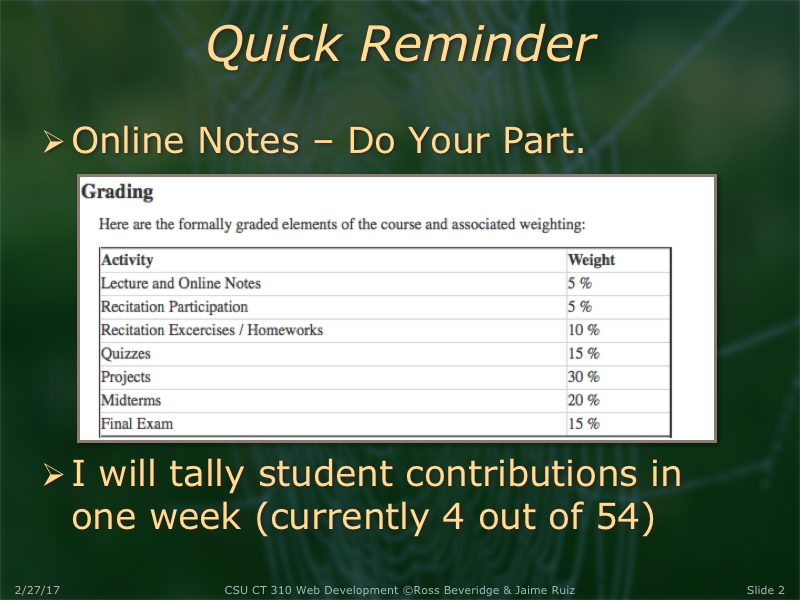
You have to log in under user in the bottom left corner and then you can add notes to slides. I didn't realize this was worth 5% of our grade.

Security class also teaches us "Something you do" is another form of authentication (e.g. gait of your walk)
Keystroke dynamics is yet another form of biometric identification. So not only do you have to type the characters in your password accurately - you have to type it with the same pacing and dwell time on the keys to gain access.
As biometrics are used more in authentication some interesting ideas about the future come to mind. What if devices tracked your brain activity and would only let you log in if you were in a certain state of mind?

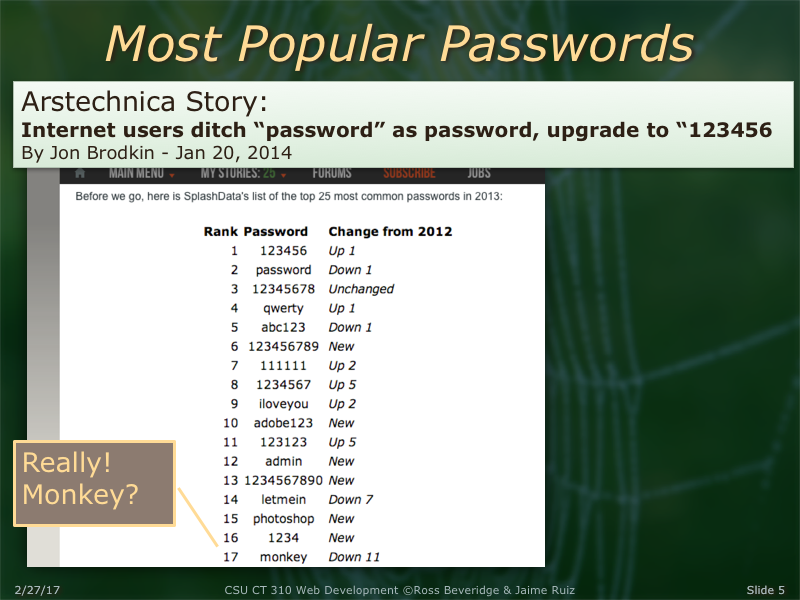
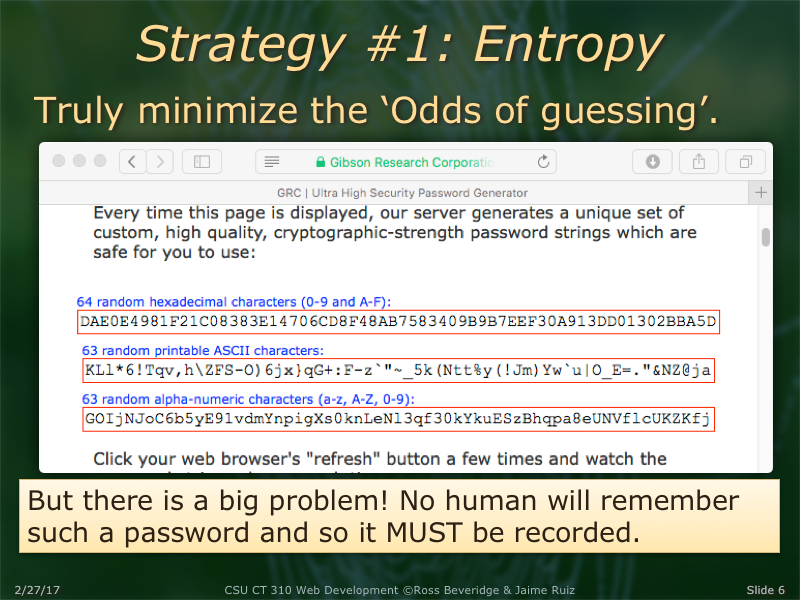
Why do you want a random number generator? Maybe to form a password...?
- Write down the first 12 characters? 16 ^ 12 possible passwords (2.8 * 10^14)
- Security principles would say it takes about 1.4 * 10^14 guesses to crack this password
- With a hundred million guesses per second (10 ^ 8), you should be able to crack this pretty fast ...
funny note, just recently before this lecture I used a random password string generator to set our wifi router admin password.

I'd never heard of this method, but it seems so simple
and yet so elegant and secure. The odds of someone getting an
entire sentence correct, included with specials, numberd, etc, must
be astronomical



Salt does not make the password impossible to crack it just lengthens the process of cracking it.
By adding salt on to the password the system can make all passwords the same length after the hash making it less easy to just match password length.
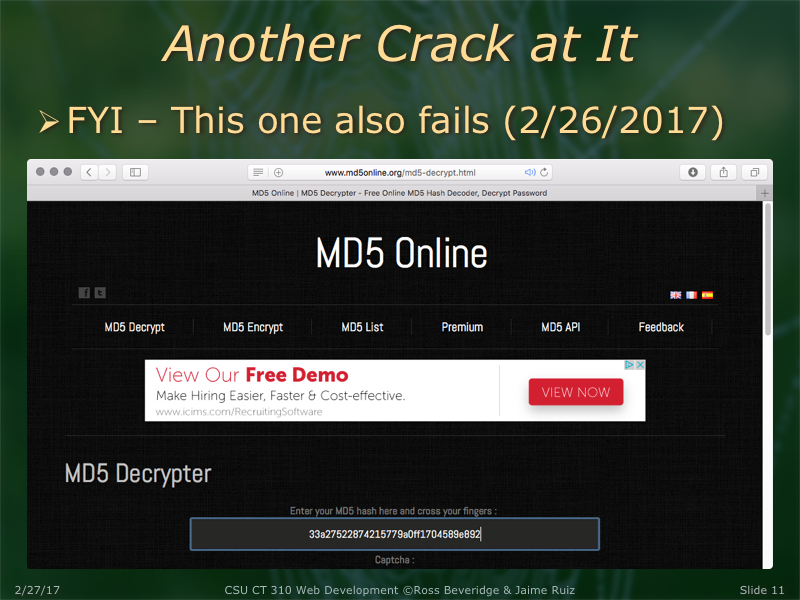



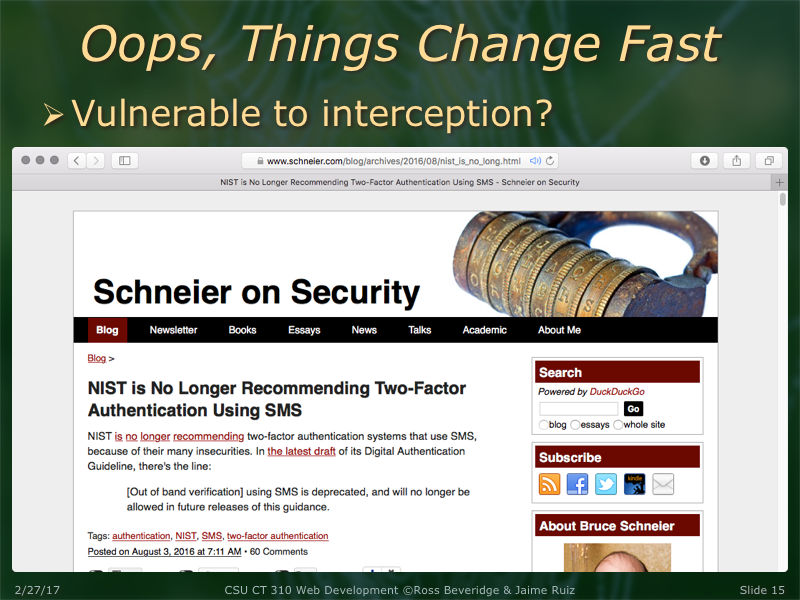
A recent example of how security technologies change is the SHA-1 hashing algorithm. Google's security research team recently produced the first SHA-1 collision, meaning that this algorithm has been proven to be unsafe to use.

I think one of the issues with biometrics is that most people don't have fingerprint recognition or iris scanners attached to their computers. Since people replace smart phones more often than computers, I could see biometric authentication becoming more popular for mobile devices in the future.


A link to the 2016 IEEE International Conference on Biometrics can be found here.


If a 3rd form of authentication is what you need, look no further than your own RFID chip. It looks like there are a few companies working on the technology for human implants, but the morality of it seems to be in question. click here for more



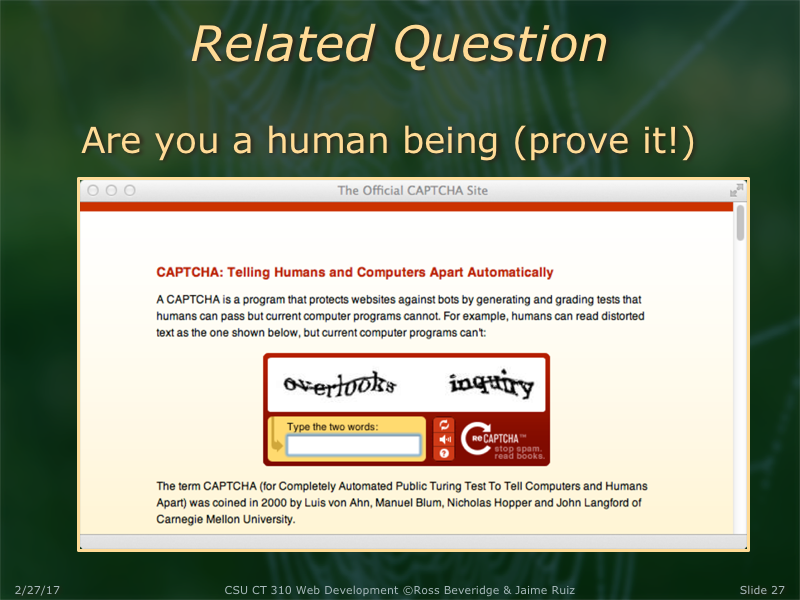
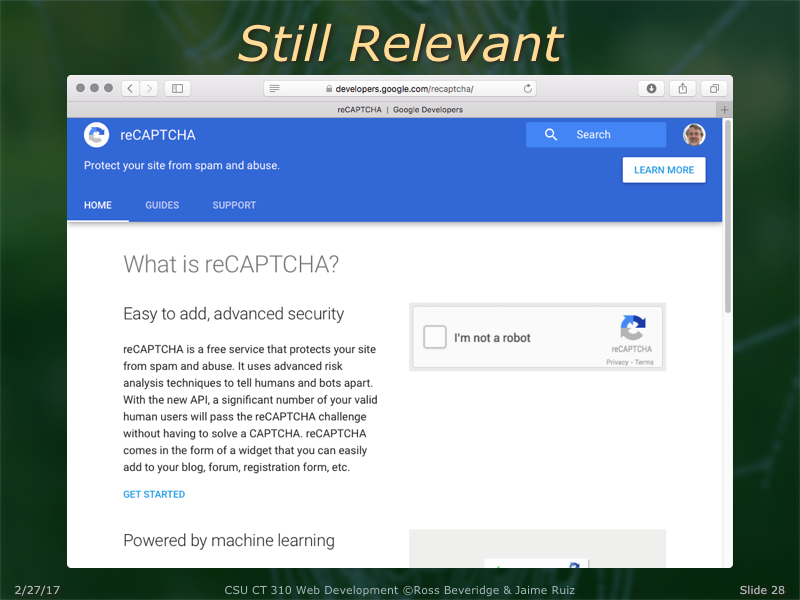
There is much more going on behind the scenes now with reCAPTCHA. Specifically, Google will often just 'recognize' you for who you are without your having to do a thing (or at least much). This posting has a nice explanation.
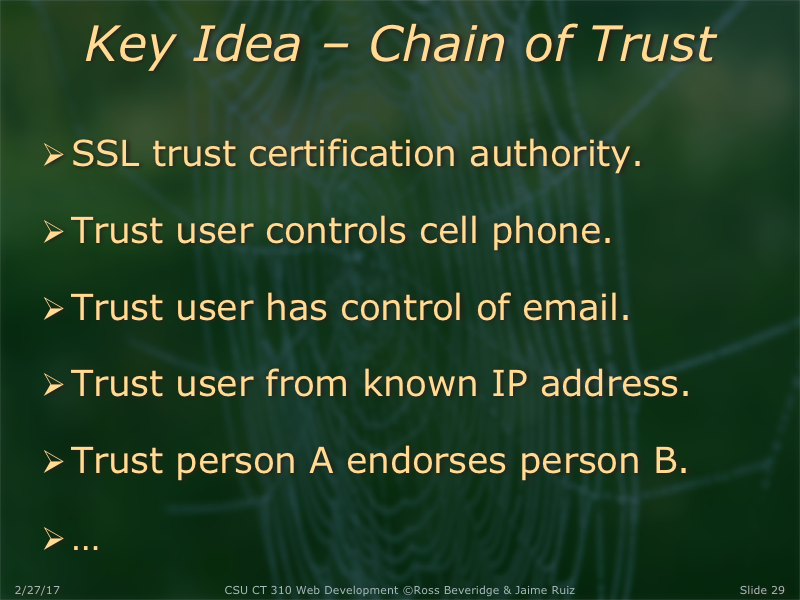
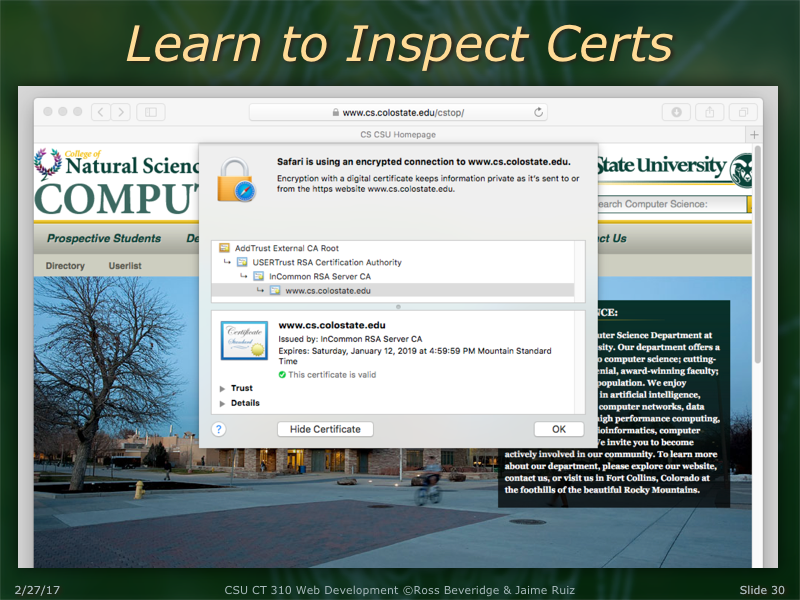
Colorado State University, Fort Collins, CO 80523 USA
© 2017 Colorado State University

