| Recent Publications |
|
PsychoRithm: A Framework for Studying How Human Traits Affect User Response to Security Situations
Proceedings of the 22nd ACM SIGSAC Conference on Computer and Communications Security Subhojeet Mukherjee, Sachini Weerawardhana,Chancey Dunn, Indrajit Ray, and Adele Howe |
|
User studies to investigate which human traits affect a user's response to cyber security related situations are typically conducted via self-reported surveys. However, it has been observed that factors such as peer perception, socially desirable responding, and responder bias etc. frequently impact the results, which then do not necessarily reflect the actual behavior of the user when subjected to real world security incidents. To mitigate such biases, we developed PsychoRithm - a software system that presents different real-world security scenarios for the subjects and records their real-time reactions to these scenarios. This paper describes the architecture of PsychoRithm, the design choices we had to make, and the challenges we faced in the design process.User studies to investigate which human traits affect a user's response to cyber security related situations are typically conducted via self-reported surveys. However, it has been observed that factors such as peer perception, socially desirable responding, and responder bias etc. frequently impact the results, which then do not necessarily reflect the actual behavior of the user when subjected to real world security incidents. To mitigate such biases, we developed PsychoRithm - a software system that presents different real-world security scenarios for the subjects and records their real-time reactions to these scenarios. This paper describes the architecture of PsychoRithm, the design choices we had to make, and the challenges we faced in the design process. |
|
Automated Extraction of Vulnerability Information for Home Computer Security
Proceedings of the 7th International Symposium on Foundations & Practice of Security FPSŅ2014 Sachini Weerawardhana, Subhojeet Mukherjee, Indrajit Ray, and Adele Howe |
|
Online vulnerability databases provide a wealth of informa- tion pertaining to vulnerabilities that are present in computer application software, operating systems, and firmware. Extracting useful information from these databases that can subsequently be utilized by applications such as vulnerability scanners and security monitoring tools can be a challenging task. This paper presents two approaches to information ex- traction from online vulnerability databases: a machine learning based solution and a solution that exploits linguistic patterns elucidated by part-of-speech tagging. These two systems are evaluated to compare ac- curacy in recognizing security concepts in previously unseen vulnerability description texts. We discuss design considerations that should be taken into account in implementing information retrieval systems for security domain. Click on the thumbnails to download zip files. Unzip and follow readme to run..
|
|
Evaluating Diversity In Classical Planning Proceedings of the 24th International Conference on Automated Planning and Scheduling, June 2014 Mark Roberts, Adele Howe and Indrajit Ray |
|
Applications that require alternative plans challenge the single solution, single quality metric assumptions upon which many classical planners are designed and evaluated. To evaluate the distinctness of alternative plans (i.e., plan sets), researchers have created diversity metrics that often measure the set difference between the actions of plans. Many approaches for generating plan sets embed the same diversity metric in a weighted evaluation function to guide the search mechanism, thus confounding the search process with its evaluation. We discover that two diversity metrics fail to distinguish similar plans from each other or to identify plans with extraneous actions, so we introduce two new diversity metrics, uniqueness and overlap, to capture these cases. We then examine the tradeoffs of producing diverse plans while we control for plan length and metric interaction and confirm that metric interaction can significantly impact search performance. We show that planners searching for plan sets must consider a third metric, parsimony, that prefers shorter plans while maximizing diversity.We evaluate three existing approaches for generating diverse plans and two new algorithms that are designed to explicitly manage diversity and interaction between the diversity and quality metrics. Our findings synthesize and extend recent results in plan diversity. |
|
Accepting the Inevitable: Factoring the User into Home Computer Security Third ACM Conference on Data and Application Security and Privacy, February 18-20,2013, San Antonio, TX (United States) Urbanska Malgorzata, Roberts Mark, Ray Indrajit, Howe Adele, Byrne Zinta. |
|
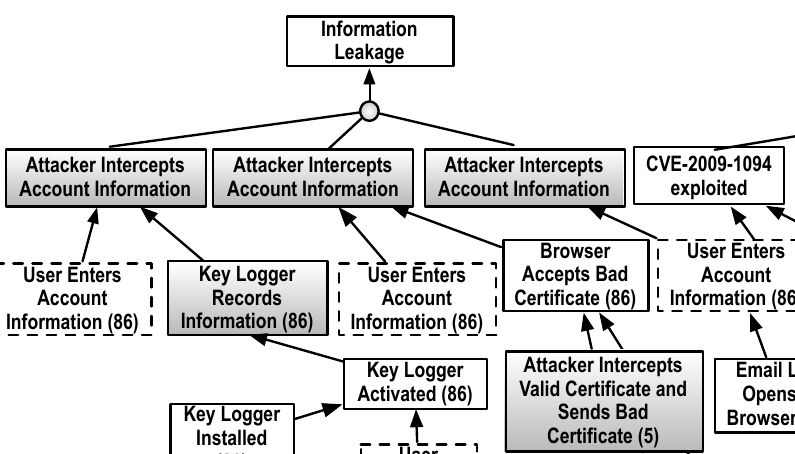
Home computer users present unique challenges to computer security. A userís actions frequently affect security without the user understanding how. Moreover, whereas some home users are quite adept at protecting their machines from security threats, a vast majority are not. Current generation security tools, unfortunately, do not tailor security to the home userís needs and actions. In this work, we propose Personalized Attack Graphs (PAG) as a formal technique to model the security risks for the home computer informed by a profile of the user attributes such as preferences, threat perceptions and activities. A PAG also models the interplay between user activities and preferences, attacker strategies, and system activities within the system risk model. We develop a formal model of a user profile to personalize a single, monolithic PAG to different users, and show how to use the user profile to predict user actions. |
|
Computer Security for the Home User 2012 Secure and Trustworthy Cyberspace Principal Investigators' Meeting, November 27-29,2012, National Harbor, MD (United States) A. Howe, I. Ray, Z. Byrne. |
|
Structuring a Vulnerability Description for Comprehensive Single System Security Analysis Rocky Mountain Celebration of Women in Computing (RMCWiC), November 01-02,2012, Fort Collins, CO (United States) Malgorzata Urbanska, Indrajit Ray, Adele Howe, and Mark Roberts. |
|
The National Vulnerability Database (NVD) provides unstructured descriptions of computer security vulnerabilities. These descriptions do not directly provide the information necessary to formally analyze how the userís and the attackerís actions lead to the exploit. Moreover, the descriptions vary in how they describe the vulnerabilities. In this paper, we describe a system for automatically extracting cause and effect information from a set of vulnerabilities. The result is a structured data set of vulnerability descriptions with pre- and post-condition relationships. We evaluate the system by comparing the output with a manually constructed representation for security analysis called the Personalized Attack Graph (PAG). |
|
Using Planning for a Personalized Security Agent The AAAI-12 Workshop on Problem Solving using Classical Planners (CP4PS-12), July 22 or 23,2012, Toronto, Ontario, Canada M. Roberts, A. Howe, I. Ray, M. Urbanska. |
|
The average home computer user needs help in reducing the security risk of their home computer. We are working on an alternative approach from current home security software in which a software agent helps a user manage his/her security risk. Planning is integral to the design of this agent in several ways. First, planning can be used to make the underlying security model manageable by generating attack paths to identify vulnerabilities that are not a problem for a particular user/home computer. Second, planning can be used to identify interventions that can either avoid the vulnerability or mitigate the damage should it occur. In both cases, a central capability is that of generating alternative plans so as to find as many possible ways to trigger the vulnerability and to provide the user with options should the obvious not be acceptable. We describe our security model and our state-based approach to generating alternative plans.We show that the state-based approach can generate more diverse plans than a heuristic-based approach. However, the state-based approach sometimes generates this diversity with better quality at higher search cost. |
|
The Psychology of Security for the Home Computer User 33rd IEEE Symposium on Security and Privacy, May 21-23,2012, San Francisco Bay Area, CA (United States) A. Howe, I. Ray, M. Roberts, M. Urbanska, Z. Byrne. |
|
The home computer user is often said to be the weakest link in computer security. They do not always follow security advice, and they take actions, as in phishing, that compromise themselves. In general, we do not understand why users do not always behave safely, which would seem to be in their best interest. This paper reviews the literature of surveys and studies of factors that influence security decisions for home computer users. We organize the review in four sections: understanding of threats, perceptions of risky behavior, efforts to avoid security breaches and attitudes to security interventions. We find that these studies reveal a lot of reasons why current security measures may not match the needs or abilities of home computer users and suggest future work needed to inform how security is delivered to this user group. |
|
Perceptions of Internet Threats: Behavioral Intent to Click Again 27th Annual Society for Industrial and Organizational Psychology (SIOP) Conference, April 26-28,2012, San Diego, CA (United States) Zinta S. Byrne, Janet M. Weidert, Joshua P. Liff, Michael Horvath, Christine L. Smith, Adele Howe and Indrajit Ray |
|
Employees use the Internet at work for personal use, exposing organizations to threats such as malware and pharming. Individuals' (older adults and women, in particular) perceptions of vulnerability and risk to specific Internet security threats influenced their decision to take an action that exposed them to unknown consequences. |
|
Personalized Vulnerability Analysis through Automated Planning Working Notes of IJCAI 2011, Workshop Security and Artificial Intelligence (SecArt-11), Mark Roberts, Adele Howe, Indrajit Ray, Malgorzata Urbanska, Zinta S. Byrne, Janet M. Weidert |
|
Attack trees and attack graphs are a well-known representation for computer security vulnerabilities. They capture how malicious activity can result in compromised systems. Unfortunately, attack graphs scale poorly, are targeted primarily to capture key components of vulnerabilities in industrial settings and focus on attacker actions. We extend the attack graph formalism by integrating user actions and supporting personalization that restricts the focus to those vulnerabilities present in a particular user/system combination (i.e., considering speciÔ¨Āc computer conÔ¨Āguration and a user‚Äôs normal activities). The enhanced attack graph is captured in the Planner Domain DeÔ¨Ānition Language (PDDL) with user speciÔ¨Āc attributes being included as facts. Given the PDDL representation, we can use a planner to 1) prune the attack graph to only those vulnerabilities for which we can derive a plan, 2) perform what-if analyses of user actions and 3) help identify interventions that are most likely to reduce the system‚Äôs susceptibility to attacks. |
|
Start-up Effects in Policy-Capturing: Stabilizing Regression Coefficients After Warm-up 25th Annual Society for Industrial and Organizational Psychology (SIOP) Conference, Apr 14, 2011 - Apr 16, 2011 in Chicago, IL (United States) Zinta S. Byrne, Janet M. Weidert, Josh Liff, Adele Howe and Indrajit Ray |
|
Policy-capturing is a technique for understanding what information people use to make decisions. People are asked to read a series of vignettes, wherein cues thought to in uence decision choices are systematically varied. Based on responses, researchers identify which cues are most in uential in decision-making. A potential drawback is that participants may need practice to become familiar with reading the vignettes. Not everyone accommodates such practice, rendering study results somewhat inaccurate. Those who do, have no guidelines for how many vignettes to provide for warm-up. We examined the need for practice and identi ed the minimum number of necessary vignettes. |
|
Dynamic Security Risk
Assessment and Management Using Bayesian Attack Graphs IEEE Transactions on Dependable and Secure Computing, January 2012, vol. 9 Nayot Poolsappasit, Rinku Dewri and Indrajit Ray |
|
Security risk assessment and mitigation are two vital processes that need to be executed to maintain a productive IT infrastructure. On one hand, models such as attack graphs and attack trees have been proposed to assess the cause-consequence relationships between various network states, while on the other hand, different decision problems have been explored to identify the minimum-cost hardening measures. However, these risk models do not help reason about the causal dependencies between network states. Further, the optimization formulations ignore the issue of resource availability while analyzing a risk model. In this paper, we propose a risk management framework using Bayesian networks that enable a system administrator to quantify the chances of network compromise at various levels. We show how to use this information to develop a security mitigation and management plan. In contrast to other similar models, this risk model lends itself to dynamic analysis during the deployed phase of the network. A multi-objective optimization platform provides the administrator with all trade-off information required to make decisions in a resource constrained environment. |




 Windows 32/64 bit
Windows 32/64 bit